About STIX STIX Project Documentation
4.6 (107) · $ 6.99 · In stock


How to Use STIX for Automated Sharing and Graphing of Cyber Threat
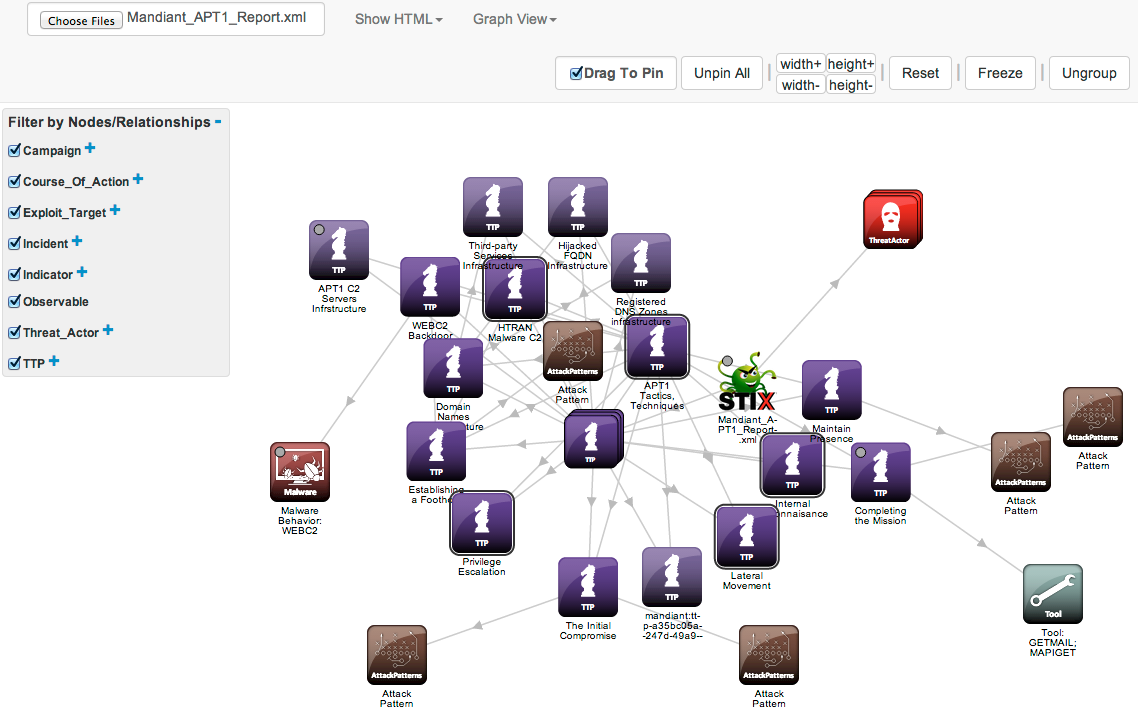
STIX, TAXII and CybOX Can Help With Standardizing Threat Information

STIX Cybersecurity: A Guide to STIX 2.1
STIX representation of a spam email where the name and email
What is Structured Threat Information eXpression (STIX)?

Kwik Stix: My New Favorite Way to Paint

Threat Intelligence with CTI Blueprint

Welcome to stixfonts Scientific and Technical Information
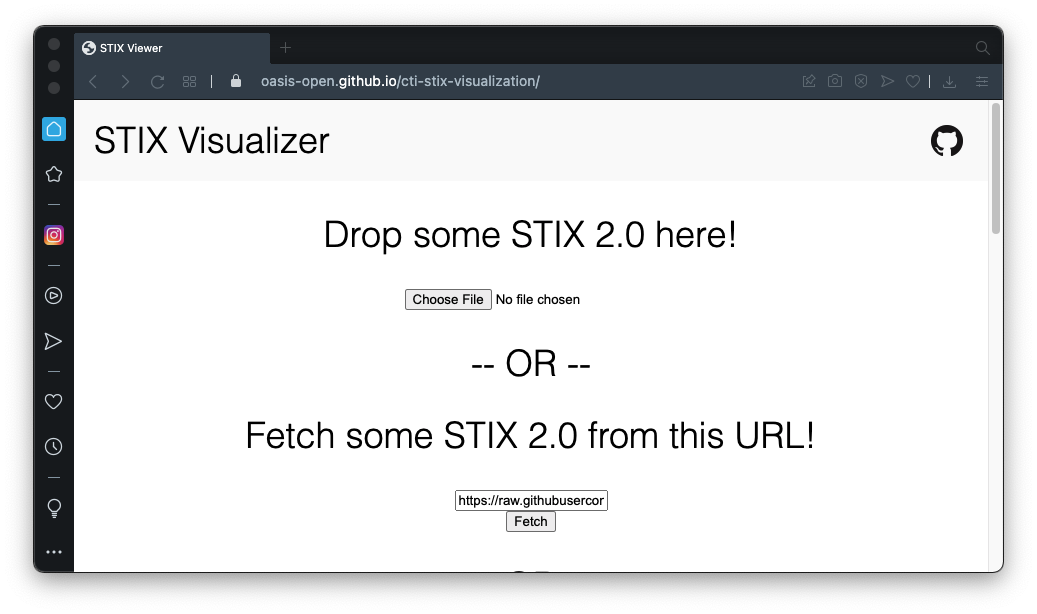
IR 380: STIX Threat Intelligence (35 pts extra)






