Defending Against Token-Based Threats
4.9 (159) · $ 30.00 · In stock


Zero Trust: The Solution to Insider Threats
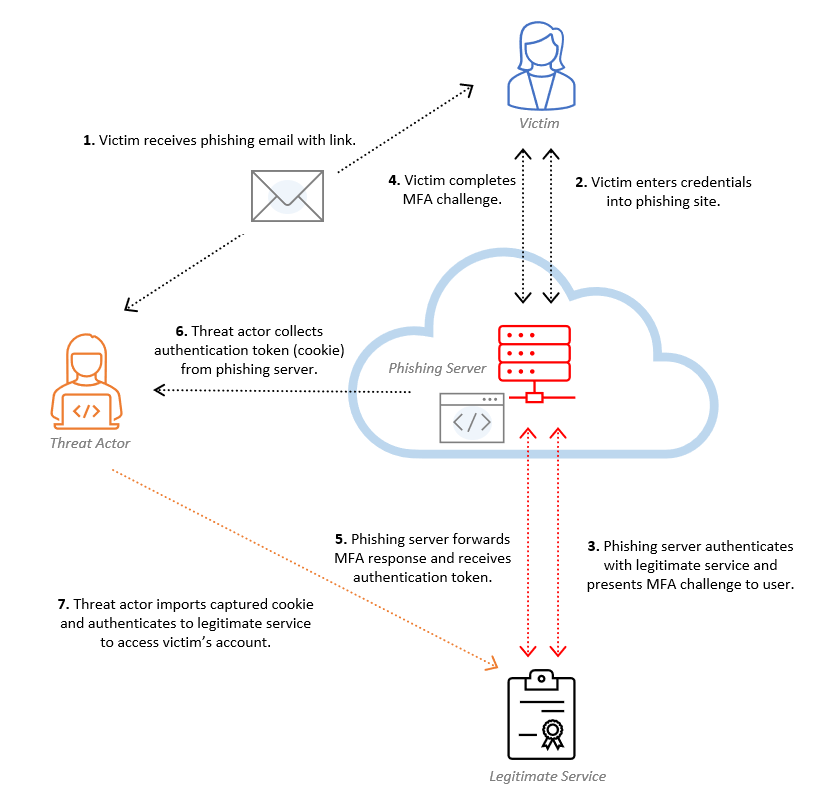
Bypassing MFA: A Forensic Look at Evilginx2 Phishing Kit
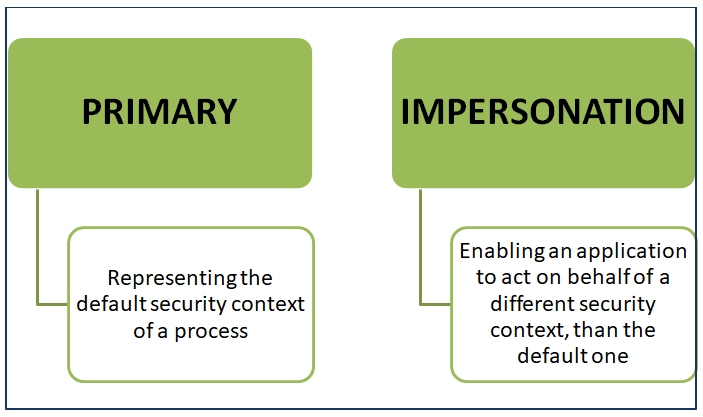
Account Manipulation and Access Token Theft Attacks - Security

DeFi Security Best Practices
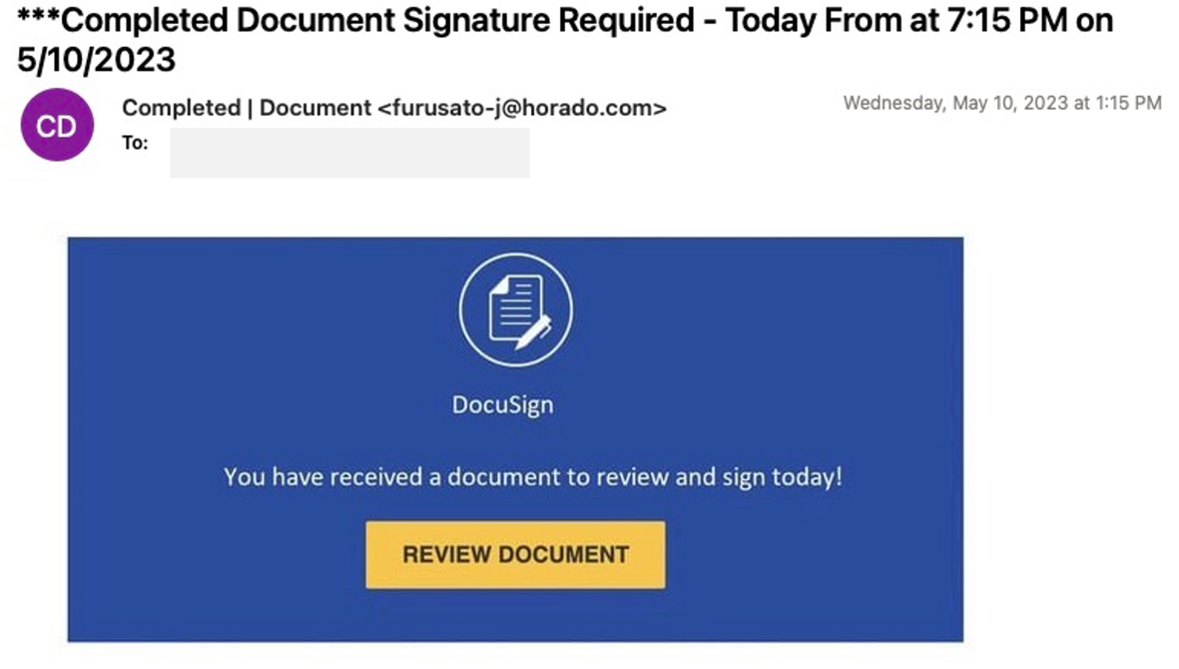
Defending Against the EvilProxy Phishing Toolkit

How Azure Active Directory opens new authentication risks

Identity and Access Security

Token tactics: How to prevent, detect, and respond to cloud token
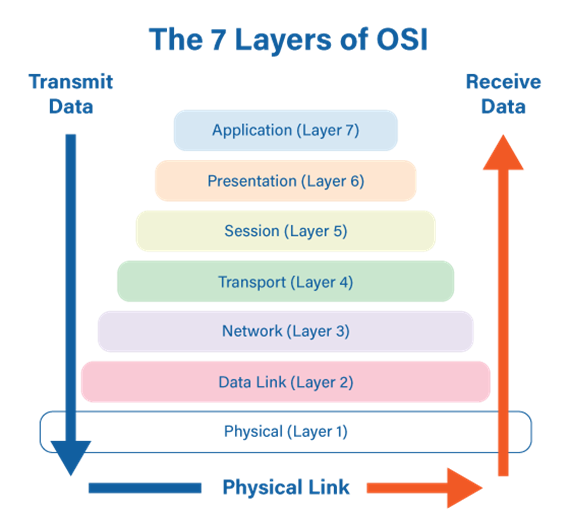
An overview of the OSI model and its security threats
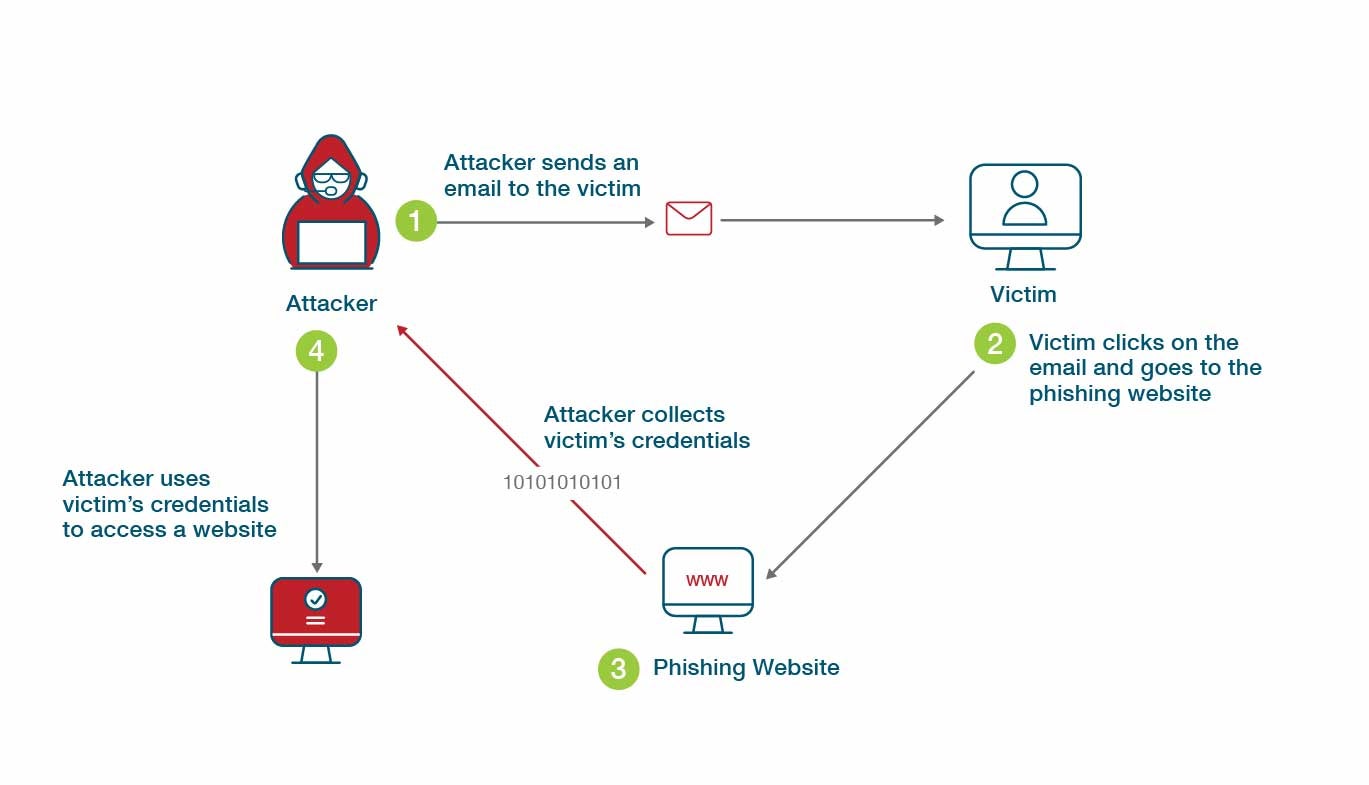
What is Phishing-Resistant MFA? Definition and Related FAQs

Attacking and Defending OAuth 2.0 (Part 1 of 2: Introduction

Robert Auch on LinkedIn: Defending Against Token-Based Threats
You may also like







