Token tactics: How to prevent, detect, and respond to cloud token
4.7 (355) · $ 38.50 · In stock


Token Sale Marketing Essentials - Proven Tactics

Swedish Windows Security User Group » Threat protection
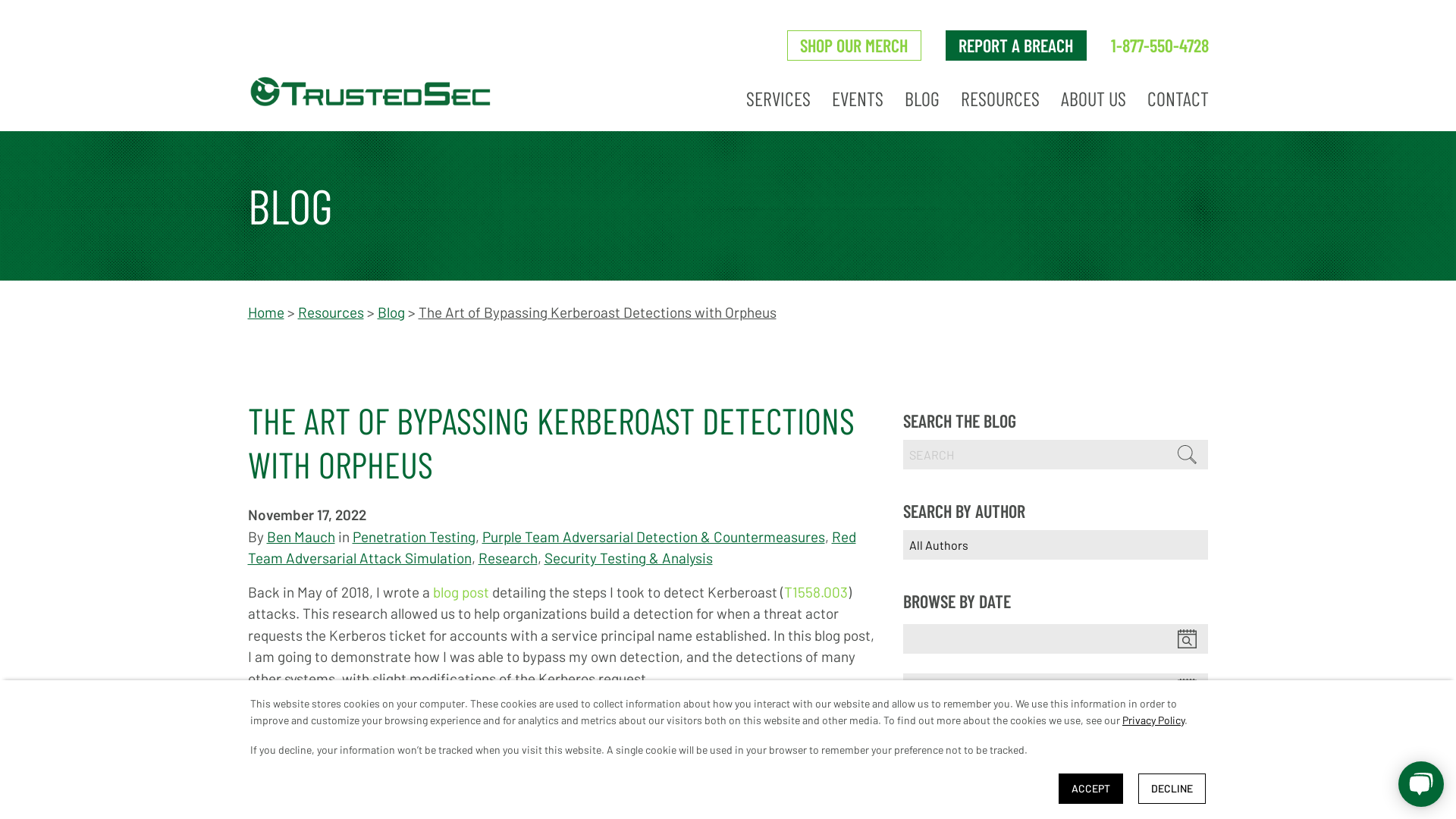
2022-11-17 Hacker Trends

Token tactics: How to prevent, detect, and respond to cloud token

TrustedSec Hacking Your Cloud: Tokens Edition 2.0
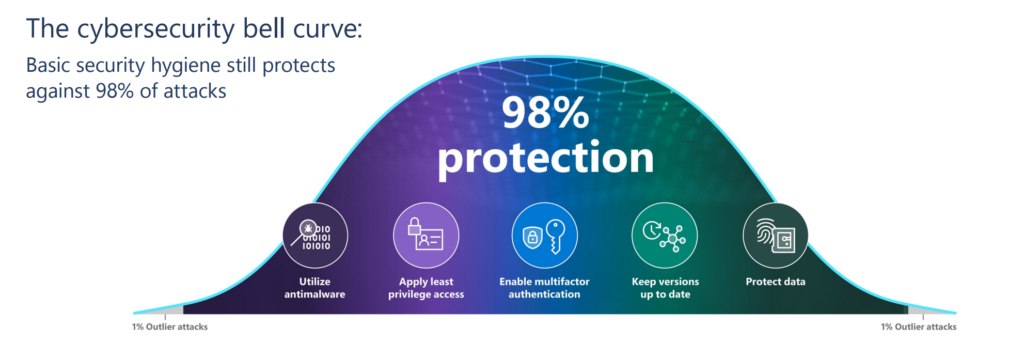
Tips for preventing against new modern identity attacks (AiTM, MFA

Jeffrey Appel on LinkedIn: How to use Automatic Attack Disruption in Microsoft 365 Defender (BEC…

Martín Obiols (@olemoudi) / X

Undermining Microsoft Teams Security by Mining Tokens by Connor
Microsoft Detection and Response Team (DART) Archives - ThreatsHub Cybersecurity News

Enhancing Network Security: Leveraging Canarytokens for Advanced
How to Prevent Session Token Theft: Comprehensive Guide

Token tactics: How to prevent, detect, and respond to cloud token







