What Is a Security Token (or Authentication Token) and How Does It Work?
4.5 (673) · $ 509.00 · In stock
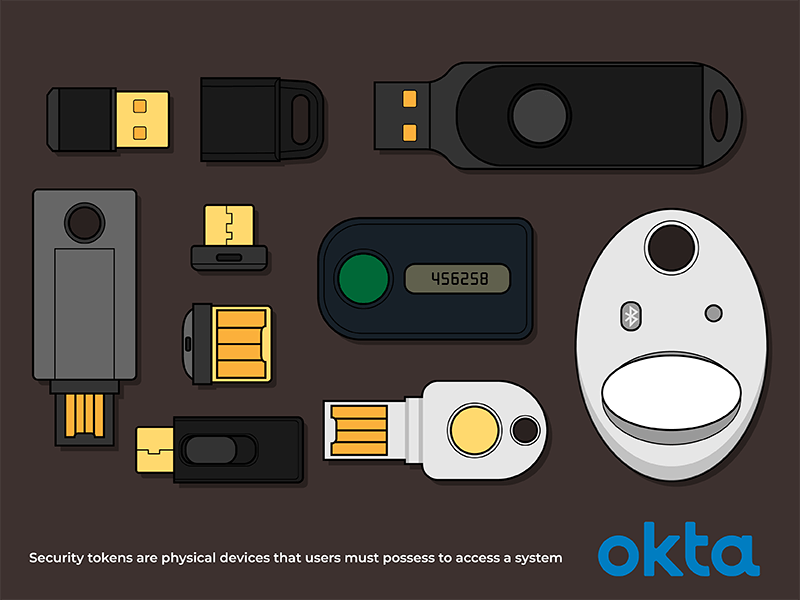

What is Token-Based Authentication? Types, Pros and Cons
Understanding JWT Authorization for Web Apps ▷▷ ConciseBlog

HTTP access tokens Bitbucket Data Center and Server 8.17
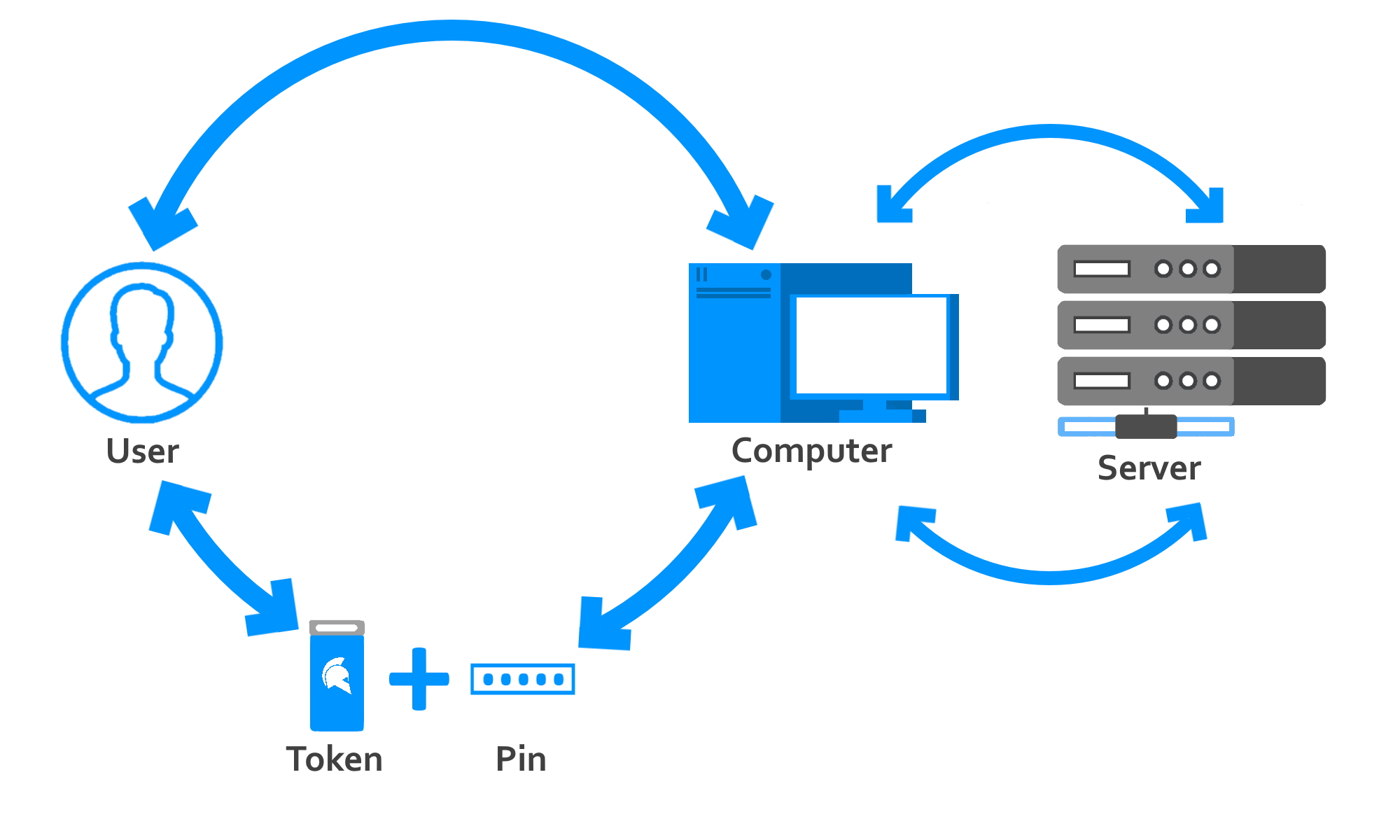
What is Token-Based Authentication? – GateKeeper

Tokenization (data security) - Wikipedia

What is Security Token? Why Are They Important?

Token tactics: How to prevent, detect, and respond to cloud token
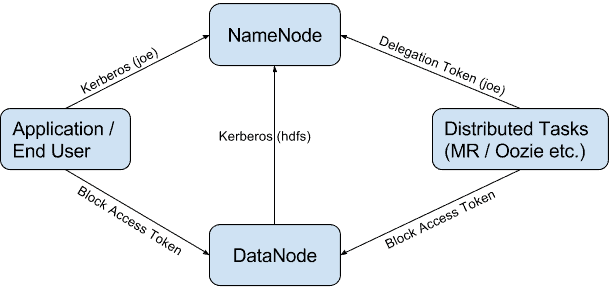
Hadoop Delegation Tokens Explained - Cloudera Blog
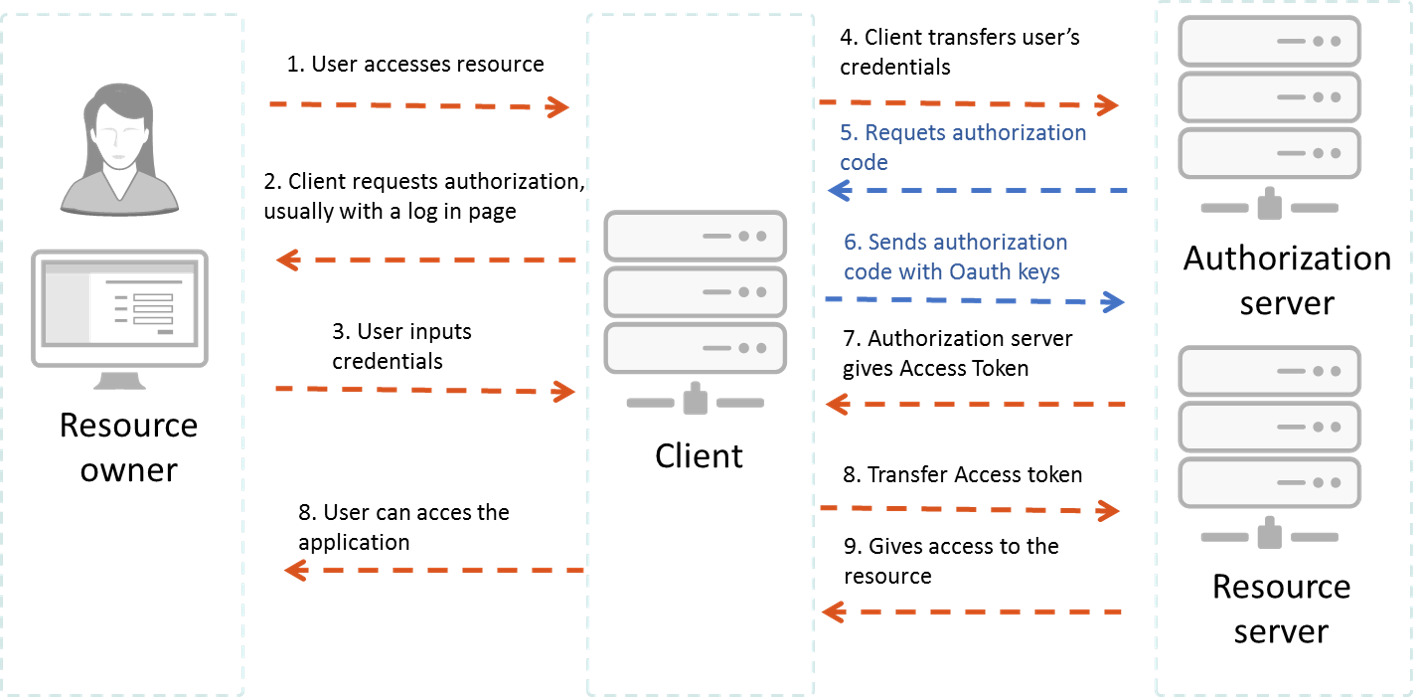
Bizagi Studio > Security definition > Work Portal Security > Work
You may also like







