Four types of fake key attacks. Each diagram represents Alice (left)
4.5 (744) · $ 21.99 · In stock
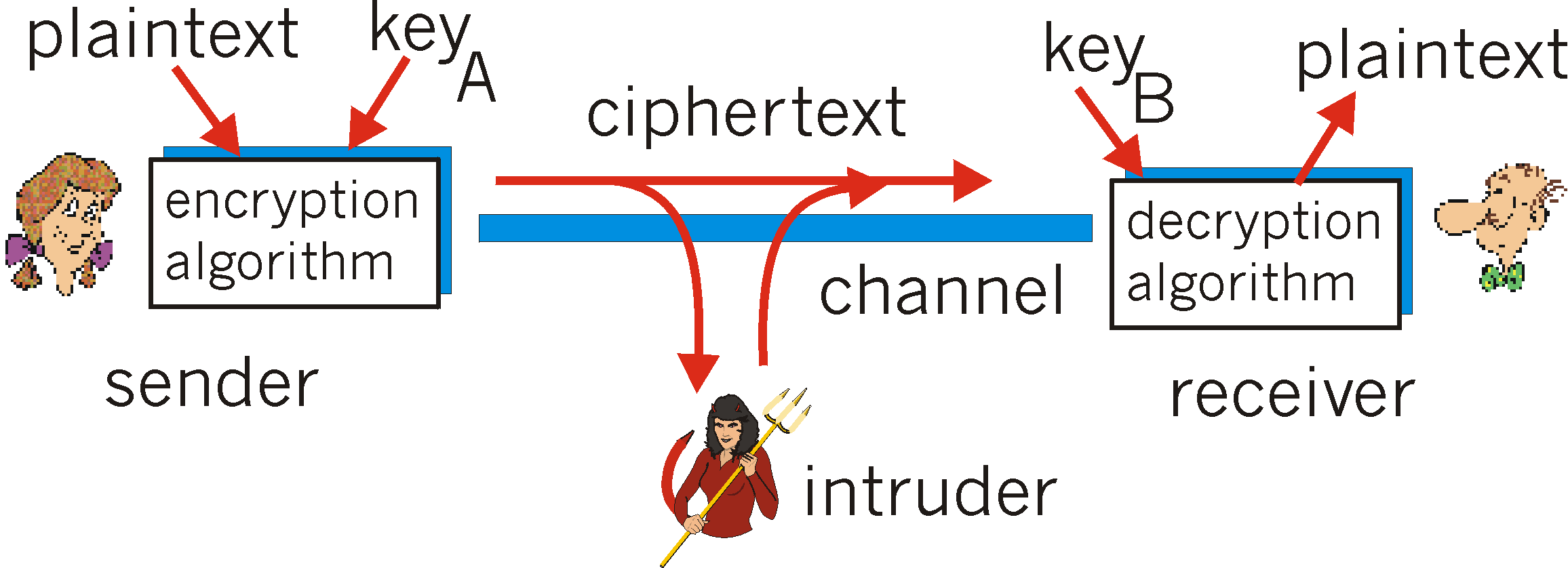
Cryptogrpahy

Color online) Basic principles of faked-state attacks against BB84. As

PDF) Automatic Detection of Fake Key Attacks in Secure Messaging

Communication scenario of interest. Alice is the transmitter with Bob
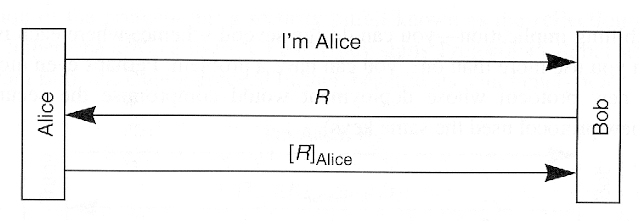
Chapter 11

Quantum Cryptography. Alice and Bob explain, Eve interferes..

Safety Assessment of Graphene-Based Materials: Focus on Human Health and the Environment

Throughput comparison between OrgAn and PriFi systems for

Tips and Tricks: Debugging .NET Malware in a Multi-Stage Malware Deployment

Synthesize high-dimensional longitudinal electronic health records via hierarchical autoregressive language model

Generic system model of physical layer security related to