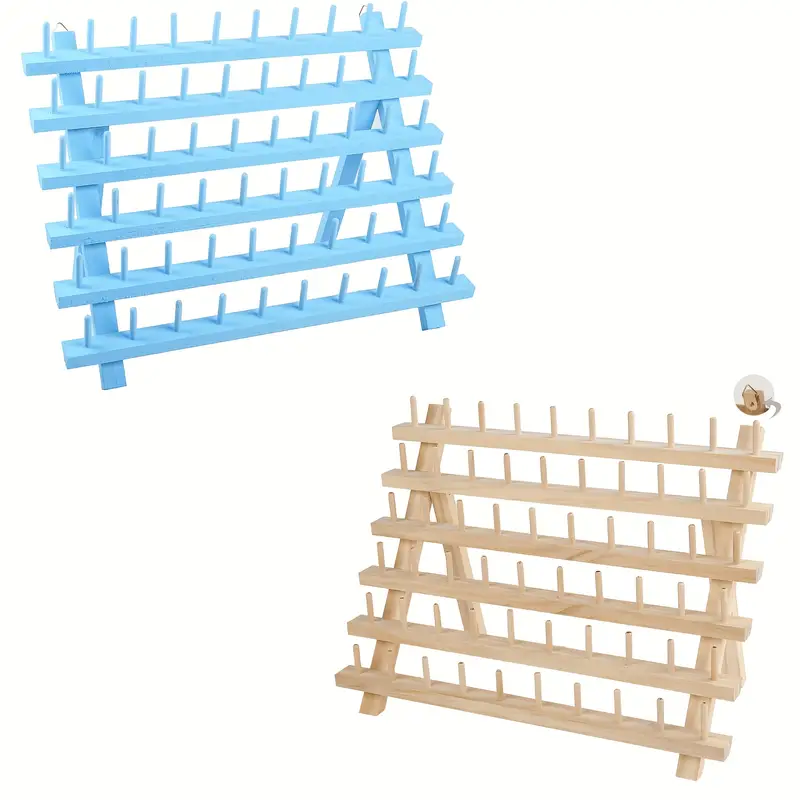
If you want to give up this much floor space for thread. on the other hand could utilize in other ways, h…
4.8 (133) · $ 76.99 · In stock

Mar 27, 2014 - If you want to give up this much floor space for thread. on the other hand could utilize in other ways, hook Sewing Thread holder using baby crib rails

RCE Bugs in Hugely Popular VoIP Apps: Patch Now! - vulnerability database

RuPaul's 'Drag Race UK' Blow Up Shows the Series is Perfect TV

QB Os, PDF, Scheduling (Computing)

Common Words: 51-75 – Ringo Lingo

How to Scrape X.com (Twitter) using Python (2024 Update)
Torque – Drum Tone Shifter - Waves Audio
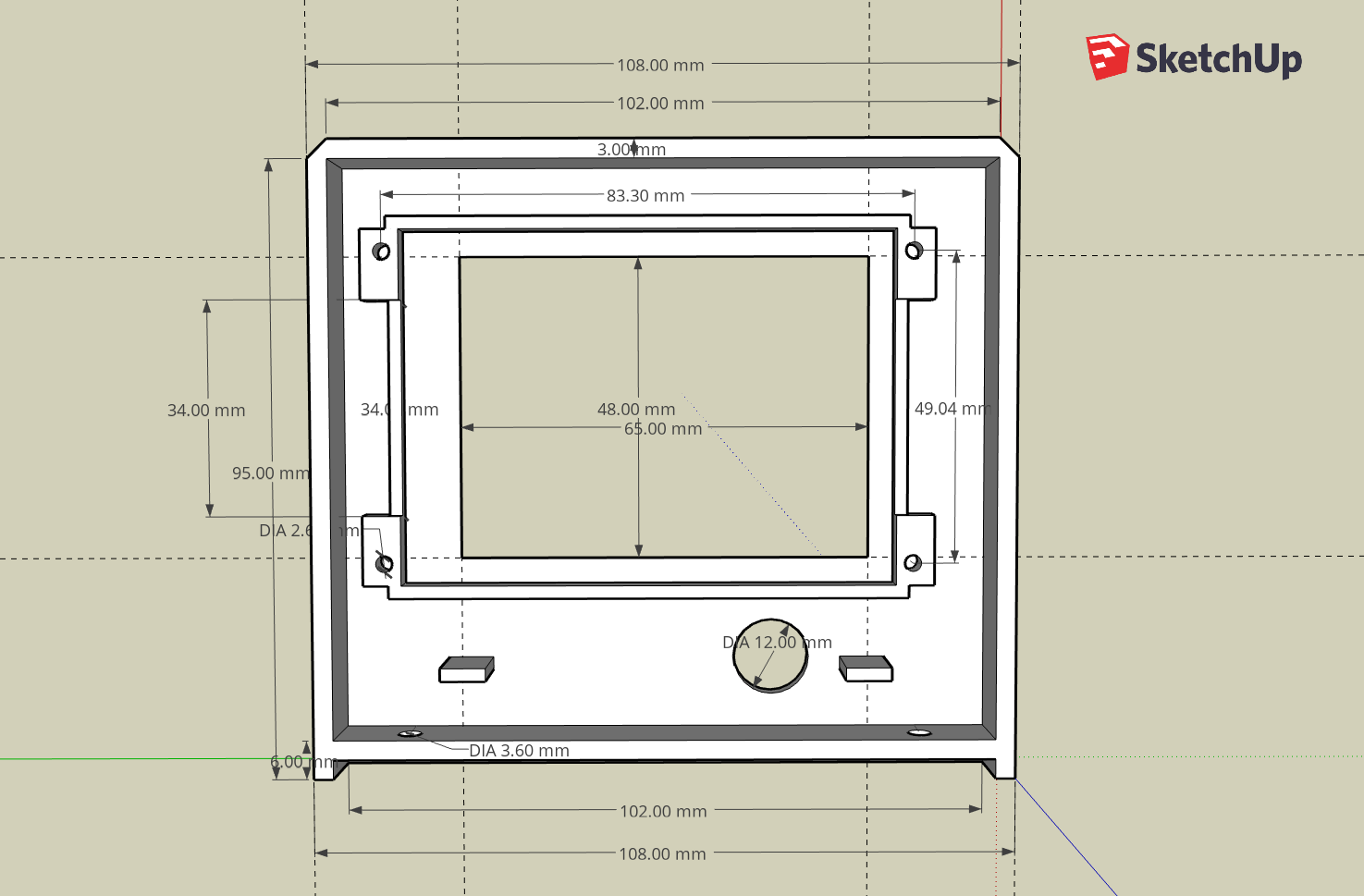
Graphical front panel display - Feature Requests - CoreELEC Forums

Please Take All Trash With You When Leaving This Area Sign, 10x7 Inches, Rust Free .040 Aluminum, Fade Resistant, Made in USA by Sigo Signs : Industrial & Scientific
turing-data/train_20170724.json at master · deeppavlov/turing-data · GitHub

African Safari (ii) ;The Interlude QR LXR-DOH-KUL

Browser-in-the-Browser Attack Makes Phishing Nearly Invisible - vulnerability database